Network segregation: IoT vs NoT
IoT devices became quite popular throughout the last years. Everything is connected, anytime. What sounds like a good idea, might actually result in a security hole in your network. As only the vendor knows what a device is actually doing, your IoT devices might bring some features with them that you don’t like.
What is the problem with my IoT device?
The short answer is: you own it, but you don’t control it. But…
Let’s use a voice assistant IoT device as an example. The little boxes sitting in each and every room react to your voice inputs. The current weather forecast is just one voice command away. But what actually happens in the background? The smart speaker records your voice, sends the recording to some public cloud provider which analyzes what you said, and just executes whatever it is commanded to do so by the cloud. In our example: read out loud the current weather forecast.
Another more physical example would be a motion sensor that reports to some internet service wether there was anybody detected. No commands are executed in your local network, but one gaining access to the data in the cloud service, could easily find out if you are at home. If I’d be the bad guy, I’d wait until the cloud tells me ‘nobody home’ before I break into your house.
So what actually happened here? Your IoT device executes commands or exposes information that are not under your control. How do you make sure that such a command is not to upload your bank account details from your PC to the cloud? Would you hang a big sign on your front door, telling everybody “House is empty, nobody is home”?
Put IoT and NoT devices in a segregated network
IoT - the internet of things is a well known term. It describes devices that need to be connected to the internet to work properly. NoT - network of things describes devices, that are connected to your network, but don’t need the internet to function properly. Both device classes shall be isolated from your local network. However, if your router doesn’t support to have 3 separate networks, there are also alternatives to set this up with less than 3.
In case your router supports having a guest network but no additional networks on top, you can use the guest network as combined replacement for the IoT and NoT networks described here.
Devices for the IoT network, are devices that do not work without an internet connection. Examples for that are smart speakers, web radio receivers or web-based weather stations.
Devices for the NoT network are devices that need to talk to your home network, but not to the internet. E.g. smart light bulbs or WiFi surveillance cameras.
How to segregate IoT and NoT devices in a Unify managed network
Ubiquiti network components are affordable devices that bring lots of professional functions with them. One of these functions is to split up your network into several VLANs. This is what we will use in our setup.
On your UniFi controller, got to Settings -> Network. Create a new IoT network with the settings shown here:
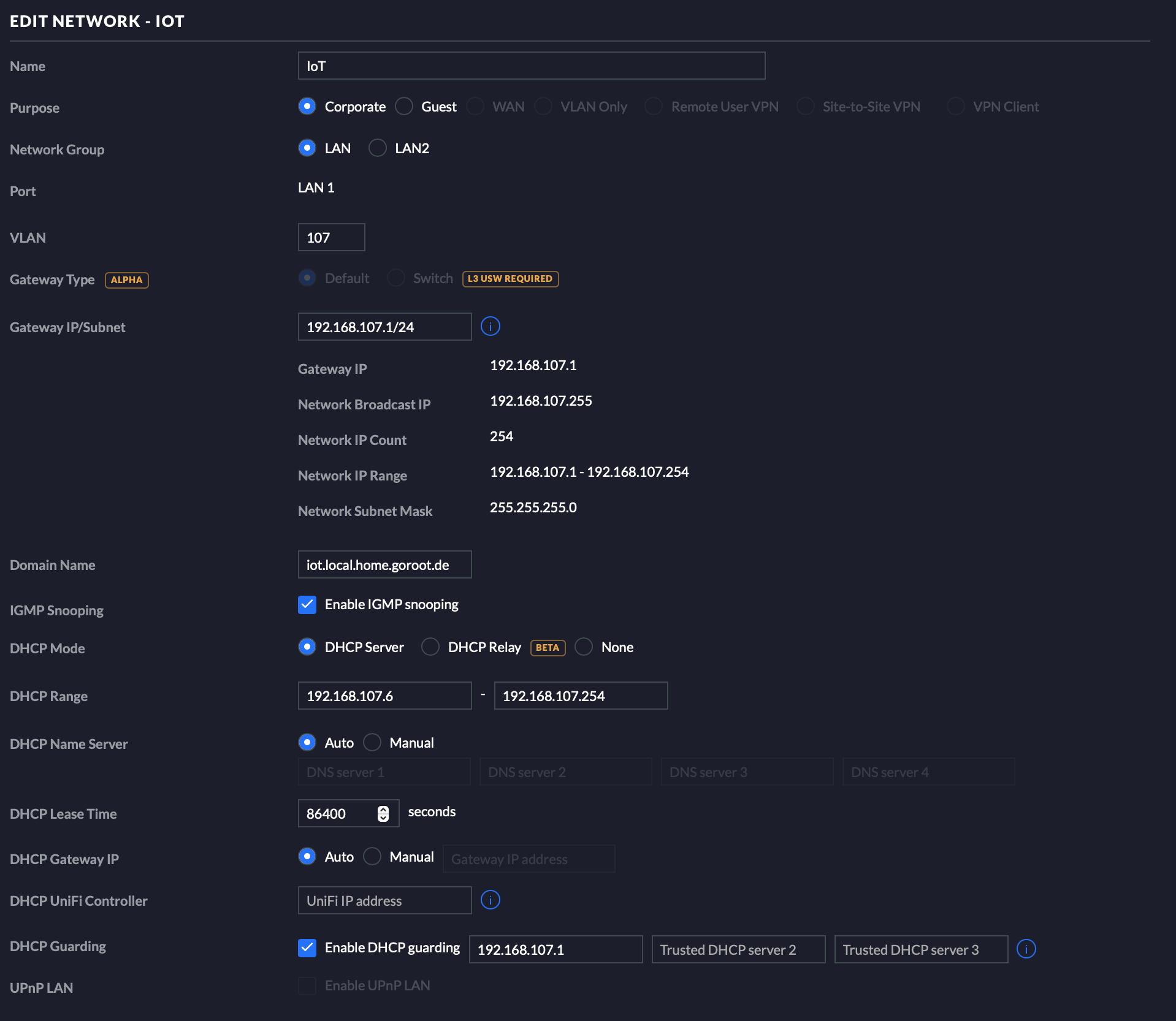 You might use any other IP range or VLAN id. I’d like to keep it simple, and use the same VLAN ID as in the 3rd octet of my IP range.
You might use any other IP range or VLAN id. I’d like to keep it simple, and use the same VLAN ID as in the 3rd octet of my IP range.
Just do the same now with the NoT network:
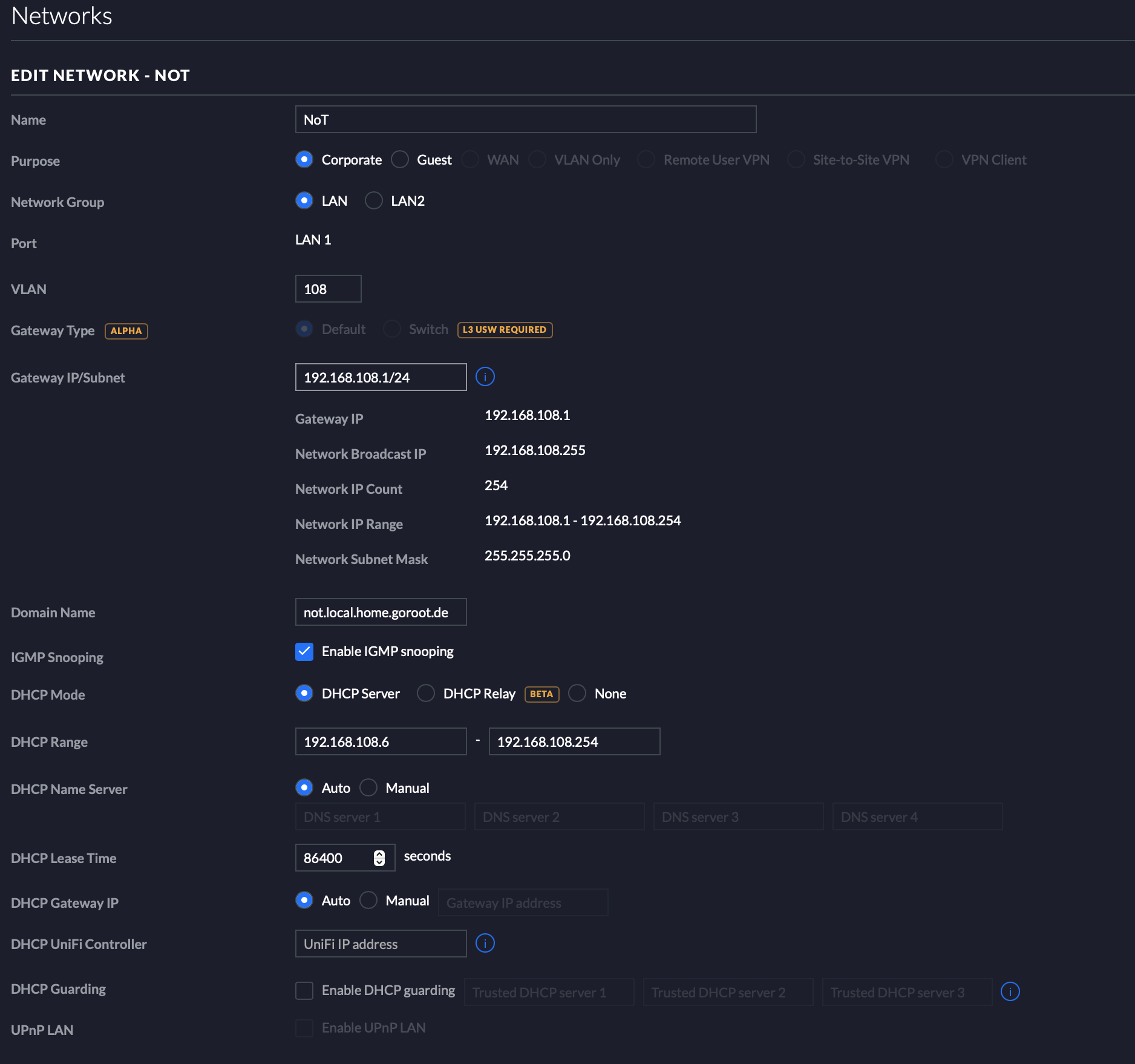
Since we have two networks now, you might also configure two WiFis that enable also wireless clients to be connected to your network. I’ll show only the IoT wifi here, since the settings for the NoT WiFi are pretty much the same:
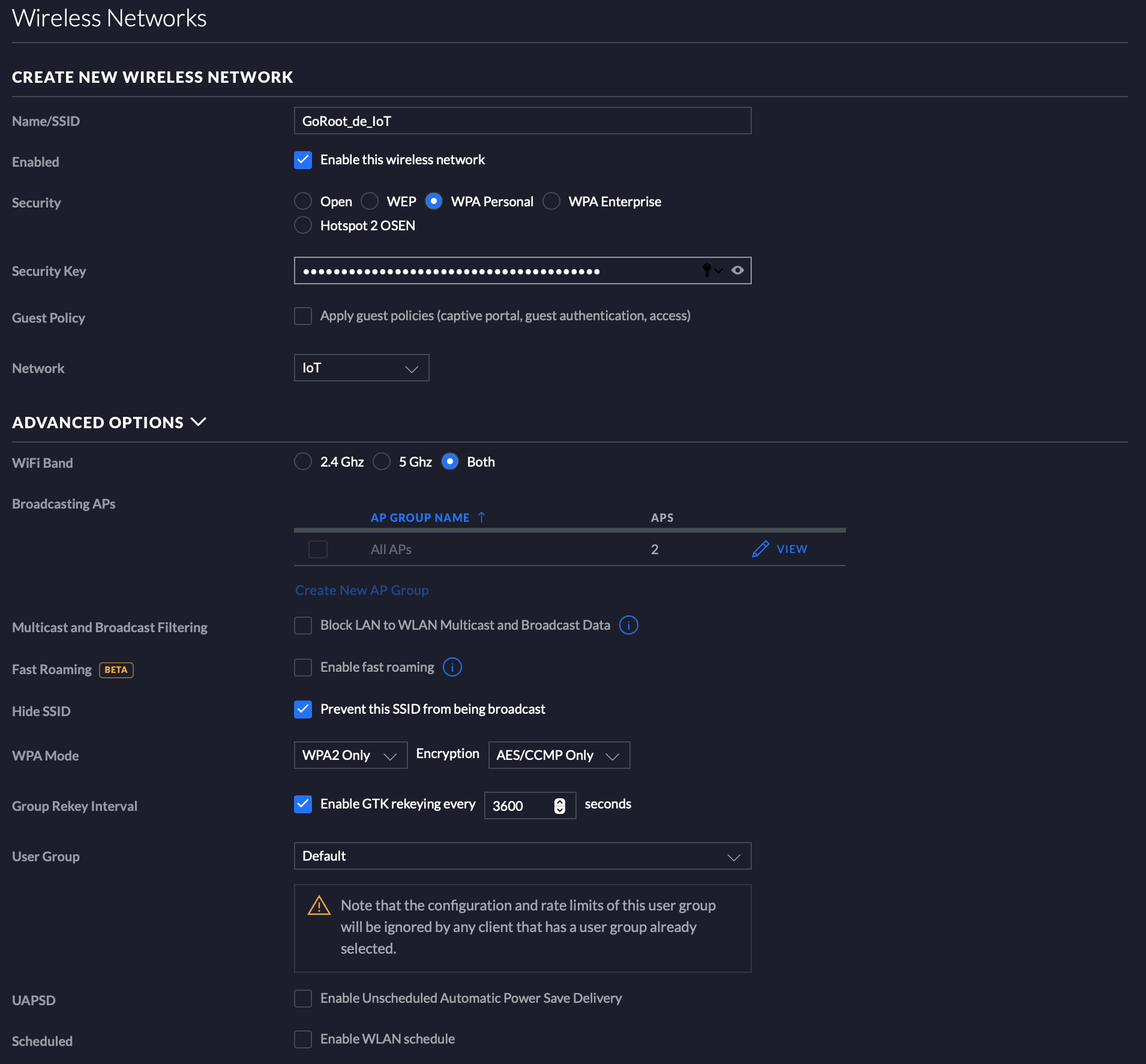
You are now all set: 2 additional VLANs / Networks are available, you just need to connect your devices to them.
Firewall configuration
The networks are as per now still able to communicate to your main network and also in between the two of them. To prevent this, we need to configure the firewall properly.
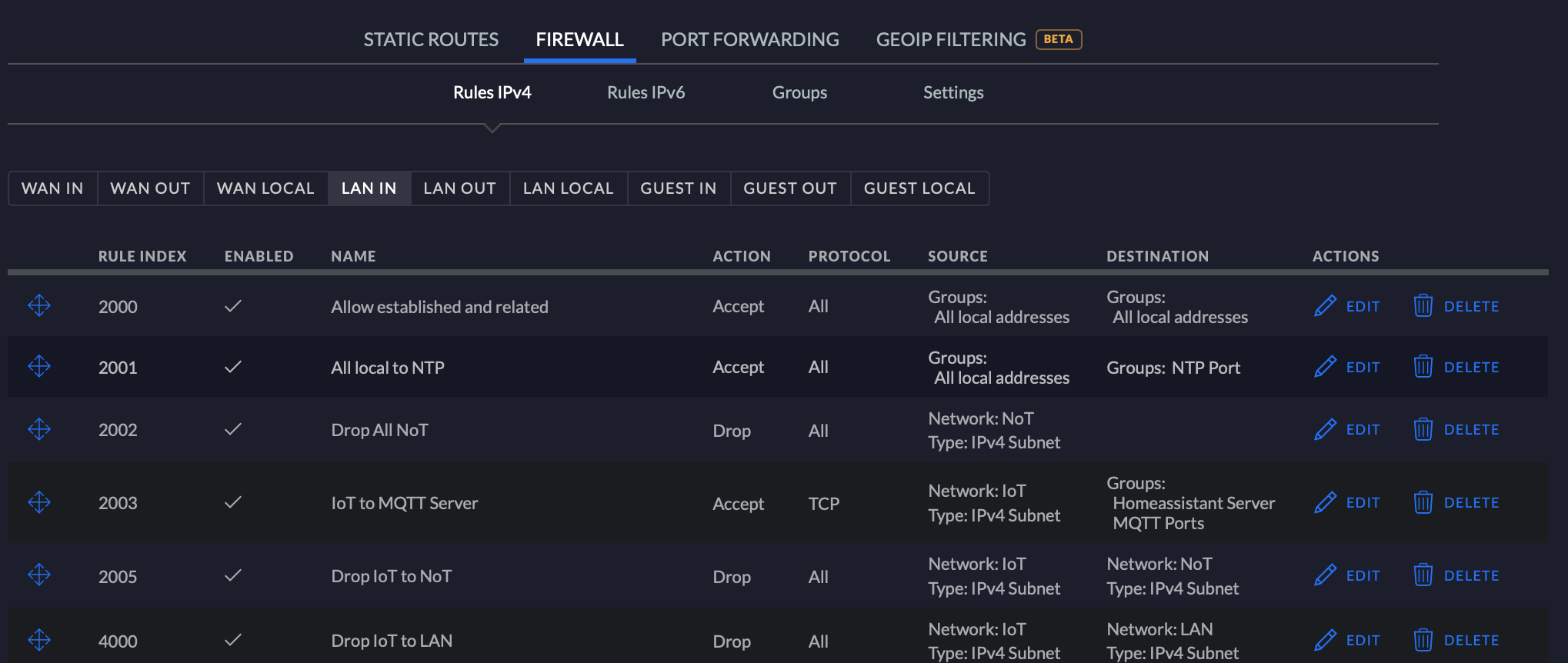
Lets go through the rules:
| ID | Name | Description |
|---|---|---|
| 2000 | Allow established and related | Allow connections that are already established. We control only initialization of a connection. If allowed by any other rule, this rule will make sure that subsequent data flow within the same connection is not blocked. |
| 2001 | All local to NTP | Allow NTP (Network Time Protocol) traffic from all local networks. This enables NoT and IoT devices to get the current time from a timeserver |
| 2002 | Drop all NoT | Drop all connections that the NoT network tries to establish. Connections initiated from the LAN to NoT network wont be affected, here the rule 2000 will make sure that data can flow freely |
| 2003 | IoT to MQTT server | Allow connections to my smart home server for the MQTT protocol. This is required for my smart devices to be able to connect to my Homeassistant server. |
| 2005 | Drop IoT to NoT | Drop all connection attempts from IoT to NoT network |
| 4000 | Drop IoT to LAN | Drop all connection attempts from IoT to LAN network |
This setup will result in a setup where:
- IoT network can only establish connections to the internet
- NoT network can establish no connections at all
- LAN can establish connections to IoT and NoT network
Since none of your IoT or NoT devices can talk to your main network (LAN) anymore, the trusted devices in this network are secure now.
Enable mDNS discovery
With the above setup you might end up having problems in discovering your NoT and IoT devices from e.g. your smartphone in the LAN network. This is due to the fact that these devices often use mDNS to get to know the presence of a device. Since mDNS cannot cross VLAN boundaries (not even with a dedicated firewall rule!), we need to make sure that the devices can send their advertisements across all networks.
Fortunately UniFi allows us to configure exactly that, by turning the switch “Enable Multicast DNS” on. You can find the toggle under Settings -> Services -> MDNS.
This will only allow the announcements to flow across VLANs, but not the actual connections. Therefore it doesn’t break any of the security measures we have setup before.

